Definitions and Principles
Cybersecurity, sometimes called IT-security, refers to the protection of computers and networks from involuntary information disclosure, disruption of services and damage to data and hard-or-software. As computer systems are increasingly seen as the backbone of organizations and the daily working environment of large amounts of the population, ensuring cybersecurity is a crucial factor for organizations and individuals alike. With the advancement of the internet, new wireless network standards and technologies such as “internet of things”, “smart devices” or connected vehicles, the importance of ensuring cybersecurity is only increasing in importance.
The primary focus of cybersecurity is arguably the provision of confidentiality, integrity and availability of data, also called the CIA-triad. In these key concepts, confidentiality aims to prevent data and information from unauthorized access while integrity aims to maintain the accuracy and consistency of data and information in all stages of the processing of the data. Lastly, availability encompasses the consistent accessibility of data and information for all authorized entities. Cybersecurity can be seen as a significant aspect of the broader concept of information security. Information security, the protection of information and data, encompasses both non-technical and technical aspects, whereby cybersecurity solely focuses on the technical aspects of it. For instance, the creation of shredding or recycling procedures of printed information would fall under the domain of information security but does not fall under the domain of cybersecurity. In these guidelines, we focus on information security in general as the management of information security includes the management of cybersecurity and offers a more holistic approach.[1]
Vulnerabilities and Threats
To ensure information security, it is essential to understand the different types of vulnerabilities that can lead to information disclosure or the disruption of services in a system.
The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) define a vulnerability in ISO/IEC 27005 as “A weakness of an asset or group of assets that can be exploited by one or more threats, where an asset is anything that has value to the organization, its business operations, and their continuity, including information resources that support the organization’s mission.”.[2]
Such vulnerabilities are classified in ISO/IEC 27005 into their related asset types: hardware, software, network, personnel, physical site and organizational site. Here, vulnerabilities may not only be caused by insecure or unprotected hardware or software but also by the susceptibility of external factors such as humidity for hardware, natural disasters for a physical site or a lack of security training for personnel. A wide range of causes for vulnerabilities exist that need to be individually evaluated for an organization or a specific research project.[3]
As the definition of a vulnerability introduces the concept of threats, it is necessary to define a threat in the context of information security. According to the European Union Agency For Cybersecurity (ENISA), a threat may be defined as: “Any circumstance or event with the potential to adversely impact an asset through unauthorized access, destruction, disclosure, modification of data, and/or denial of service”.[4]
A plethora of different threats exists for which various possible classification schemes exist. The threat classification model of the Horizon2022 project CyberSANE provides a good overview of possible threat types. For each type, multiple threats may exist.
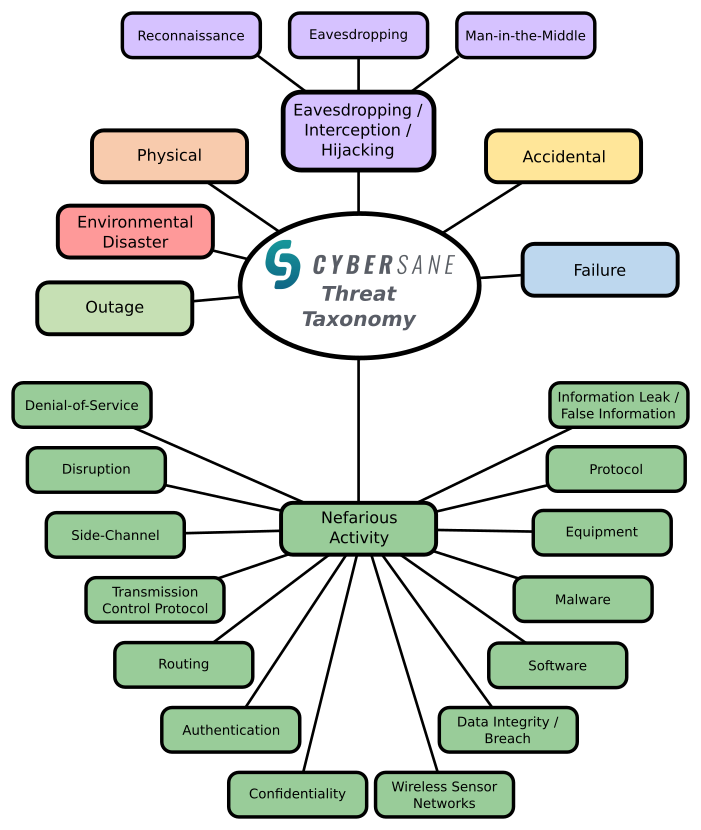
Figure 1. Threat classification model by CyberSANE Horizon2020 project.[5]
The existence of threats and vulnerabilities poses a risk to an organization as threats could exploit vulnerabilities and thereby harm an organization.[6] An organization or a research project, therefore, needs to create an information security management system (ISMS) to identify, monitor, and mitigate information security risks.
References
1For a discussion on the terms we refer to the BSI Standard 200-2. 2017 IT-Grundschutz Methodology: “The goal of information security is to protect information. This information might be stored on IT Systems, but also on paper or inside people’s heads. IT security primarily concerns protecting and processing information stored electronically. In case of cyber security, the field of action of classic IT security is extended to the whole cyberspace. This comprises any and all information technology connected to the Internet and comparable networks, and includes communication, applications, processes and processed information based on the aforementioned. Thus, the term “information security” instead of IT security or cyber security is more comprehensive.” p.13. Available under: https://www.bsi.bund.de/SharedDocs/Downloads/EN/BSI/Grundschutz/International/bsi-standard-2002_en_pdf.pdf?__blob=publicationFile&v=2 (Last accessed: 11.11..2021) ↑
2ISO/IEC, “Information technology — Security techniques-Information security risk management” ISO/IEC FIDIS 27005:2008 ↑
3Kakareka, Almantas (2009). “23”. In Vacca, John (ed.). Computer and Information Security Handbook. Morgan Kaufmann Publications. Elsevier Inc. ISBN 978-0-12-374354-1. ↑
4ENISA. Glossary. Available under: https://www.enisa.europa.eu/topics/threat-risk-management/risk-management/current-risk/risk-management-inventory/glossary (Last accessed: 03.11.2021) ↑
5CyberSANE, 2020. (Grant agreement number: 833683) Taxonomy of Threat Landscape. Available under: https://www.cybersane-project.eu/taxonomy-of-threat-landscape/ (Last accessed: 03.11.2021) ↑
6See ENISA definition of risk “The potential that a given threat will exploit vulnerabilities of an asset [G.3] or group of assets and thereby cause harm to the organization.” Available under https://www.enisa.europa.eu/topics/threat-risk-management/risk-management/current-risk/risk-management-inventory/glossary (Last accessed: 03.11.2021) ↑
