Managing information security is not an easy task and both information- and cybersecurity is are not tasks that can be “completed”. Instead, it involves a continuous process of monitoring threats and risks, identifying vulnerabilities and continuous improvements of an ISMS. To do so, multiple ISO/IEC standards can be utilized as references and to obtain certification on the specific standards.
The most important standards for information security, in general, are the following:
- ISO/IEC 27000:2018 Information technology — Security techniques — Information security management systems — Overview and vocabulary
- ISO/IEC 27001 INFORMATION SECURITY MANAGEMENT
- ISO/IEC 27001:2013 Information technology — Security techniques — Information security management systems — Requirements
- ISO/IEC 27002:2013 Information technology — Security techniques — Code of practice for information security controls
- ISO/IEC 15408-1:2009 Information technology — Security techniques — Evaluation criteria for IT security
- The BSI-Standard 200-2 on IT-Grundschutz methodology (formerly known as IT baseline protection manual)[1]
Be aware that there are additional standards that focus on cybersecurity in specific domains such as IoT-devices or vehicles.[2] While ISO/IEC 27000 provides an overview on the vocabulary of information security, ISO/IEC 27001 and ISO/IEC 27002 provide guidelines and requirements on how to establish and maintain an ISMS within an organization. These guidelines can be adapted to research projects and should be used by project coordinators and employees responsible for the management of information security in a research project.
Risk Management
ENISA provides SMEs with an online tool[3][4] to assess information security risks for the protection of personal data that can be adapted towards researchers that handle personal data as part of their research endeavors and projects. Risk management encompasses identifying, quantifying, mitigating and communicating risks. To do so, ENISA divides risk management into four phases:
- Risk assessment: The current level of risks is calculated through the identification of threats and the evaluation of the likelihood and their potential impact on the organization.
- Risk treatment: Suitable security measures are taken to mitigate, transfer, avoid or retain the identified risks. Hereby, multiple security measures should be combined if possible.
- Risk acceptance: As not all risks can be completely avoided, management decisions need to be taken on how to deal with residual risks.
- Risk communication: Risks need to be communicated to relevant stakeholders.
Managing Information Security – A Walthrough
In the following, an exemplary approach towards risk evaluation to ensure information security in the processing of personal data in a research project is provided, based on the material provided by ENISA.[5] [6]
This approach is based on five steps that are outlined in this chapter:
- Definition of the processing operation and its context
- Understanding and evaluating the impact
- Definition of possible threats and evaluation of their likelihood
- Evaluation of risk
- Selection of appropriate security measures
1. Definition of the processing operation and its context
The person responsible for ensuring information security – and potentially the controller or processor for the processing of personal data in the context of the GDPR – need to define the context of the data processing system. This includes considering the different stages of the data (collecting, storing, processing, and disposing) as well as the entities and roles that are relevant to the data processing.
The following questions need to be clearly answered by the controller or processor of the data:
- What is the personal data processing operation?
- What are the types of personal data processed?
- What is the purpose of the processing?
- What are the means used for the processing of personal data?
- Where does the processing of personal data take place?
- Which are the categories of data subjects?
- Which are the recipients of the data?[7]
| Example: An EU ICT research project is to be conducted. The project coordinator acts as a controller and is responsible to ensure information security as well as GDPR compliance. The coordinator analyses that, to fulfill the projects objectives, personal data from data subjects need to be gathered through questionnaires, surveys and interviews. In these processing operations, sensitive data such as health-related information are gathered to develop innovative solutions and insights based on the data. Additionally, sensitive company information is gathered from the consortium. As means of processing, a non-automated way (surveys, interviews) were chosen for the collection of the data, while the transfer and evaluation of the data take place in an automated form.
The data is to be processed solely by the project consortium and stored at dedicated cloud infrastructure provided by consortium members. |
2. Understanding and evaluating the impact
Secondly, the potential impact of threats, vulnerabilities and security incidents needs to be assessed. To do so, a set of pre-defined parameters can be used to evaluate the impact on confidentiality, integrity and availability of the data.
| Impact Level | Explanation |
| Low | Minor inconveniences for individuals, data subjects or organizations such as annoyances or additional time spent |
| Medium | Significant inconvenience for individuals, data subjects or organizations such as additional costs, stress or denial of access to business services |
| High | Significant consequences that lead for instance to financial damage, worsening of health or loss of employment. |
To evaluate the impact level of a potential security incident, the type and amount of personal data, the criticality of the processing or special characteristics of the data subjects or organizations can be used as assessment parameters. Such assessments need to be taken for all types of unauthorized data disclosures (confidentiality, integrity and availability) and all types of activities and actions that are conducted in a research project.
| Example: The coordinator defines three impact levels for its data processing operations. The processing of sensitive organizational data is defined as medium as the loss of data through third parties could lead to a disruption of the processes of consortium members (confidentiality and availability security breach). The impact of a confidentiality security breach of health data from data subjects is seen as high as this could lead to the loss of employment of data subjects if the data would be made public to third parties. |
3. Definition of possible threats and evaluation of their likelihood
Thirdly, threats and their likelihood of occurrence need to be evaluated. As explained above, a threat may be defined as an occurrence that could negatively affect an asset (here: data and information) through unauthorized access, destruction, disclosure or modification of data. Similar to the impact assessment, three threat occurrence likelihood levels can be defined from low, unlikely, to medium and high.
As detailed earlier, numerous threats can be classified into various types. To further simplify the classification, ENISA only defines four areas of types with exemplary threats:
- Network and technical resources (hardware and software):external attackers might attack the network while internal security flaws, backdoors, bugs or communication errors between resources might pose vulnerabilities.
- Processes related to the data processing operation:flawed processes and procedures can lead to threats such as the (un)intentional corruption of data, (un)intentional deletion or modification of data and access to the data by unauthorized internal and external entities.
- Different parties and people involved in the processing operation:Arguably the greatest threat to information security is the human factor. This includes accidental and malicious mishandling of data by internal personnel as well as by external sub-contractors or recipients of data.
- Business sector and scale of the processing:The amount and value of data might attract attackers that seek monetary profit by illegally obtaining the data. Similarly, ensuring cybersecurity increases in effort with the amount of data and organizations, individuals and processes that are involved in dealing with the data.
Example: The coordinator defines possible threats and their likelihood of occurrence for the data processing in the project.
|
4. Evaluation of risks
Now that threat occurrence probabilities and the impact of risks have been obtained, the risk level in the form of a risk matrix can be calculated. Within the risk matrix, specific threats and vulnerabilities can now be grouped to allow an immediate assessment of which risks are most or least important.
| Example: The following risk matrix demonstrates exemplary risks for a research project |
| Impact Level | ||||
| Threat Probability | Low | Medium | High | |
| Low | (Hardware related threats) | (Natural disaster destroys server with company specific data without backup) | ||
| Medium | (Project member gets hacked and project-related information gets stolen) | |||
| High | (Non-employees get unauthorized access to non-sensitive data) | (Sensitive health data accidentally shared by project members) | ||
5. Selection of appropriate security measures
Following the development of a risk matrix, security measures can now be devised to counteract, mitigate and eliminate the identified risks. It is hereby advised to firstly focus on the risks that demonstrated the highest impact and/or threat probability of occurrence.
Security measures can be categorized into technical and organizational measures.[8] These measures are defined in ISO/IEC 27001 Annex A and ISO/IEC 27002 and further clustered into sub-categories, as seen in the following figure.
| Measure Type | Category | Sub-Category | Related to |
| Organizational | Security Management | Security policy and procedures for the protection of personal data | ISO 27001:2013 – A.5 Security policy |
| Organizational | Security Management | Roles and responsibilities | ISO 27001:2013 – A.6.1.1 Information security roles and responsibilities |
| Organizational | Security Management | Access control polity | ISO 27001:2013 – A.9.1.1 Access control policy |
| Organizational | Security Management | Resource / asset management | ISO 27001:2013 – A.8. Asset management |
| Organizational | Security Management | Change management | ISO 27001:2013 – A.12.1 Operational procedures and responsibilities |
| Organizational | Security Management | Data processors | ISO 27001:2013 – A.15 Supplier relationships |
| Organizational | Incident response and business continuity | Incidents handling / personal data breaches | ISO 27001:2013 – A.16 Information security incident management |
| Organizational | Incident response and business continuity | Business continuity | ISO 27001:2013 – A.17 Information security aspects of business continuity management |
| Organizational | Human resources | Confidentiality of personnel | ISO 27001:2013 – A.7 Human resource security |
| Organizational | Human resources | Training | ISO 27001:2013 – A.7.2.2 Information security awareness, education and training |
| Technical | Access control and authentication | – | ISO 27001:2013 – A.9 Access control |
| Technical | Logging and monitoring | – | ISO 27001:2013 – A.12.4 Logging and monitoring |
| Technical | Security of data at rest | Server/Database security | ISO 27001:2013 – A.12 Operations security |
| Technical | Security of data at rest | Workstation security | ISO 27001:2013 – A.14.1 Security requirements of information systems |
| Technical | Network / Communication security | – | ISO 27001:2013 – A.13 Communications Security |
| Technical | Backups | – | ISO 27001:2013 – A.12.3 Back-Up |
| Technical | Mobile / Portable devices | – | ISO 27001:2013 – A.6.2 Mobile devices and teleworking |
| Technical | Application lifecycle security | – | ISO 27001:2013 – A.12.6 Technical vulnerability management & A.14.2 Security in development and support processes |
| Technical | Data deletion /disposal | – | ISO 27001:2013 – A. 8.3.2 Disposal of media & A. 11.2.7 Secure disposal or re-use of equipment |
| Technical | Physical security | – | ISO 27001:2013 – A.11 – Physical and environmental security |
For all categories, ISO defines multiple precise security measures that an organization should take. These security measures are mapped to the level of risk identified in the fourth step. ENISA is offering a free online tool for this mapping that includes descriptions for the specific measures that need to be taken, depending on the identified risk level.
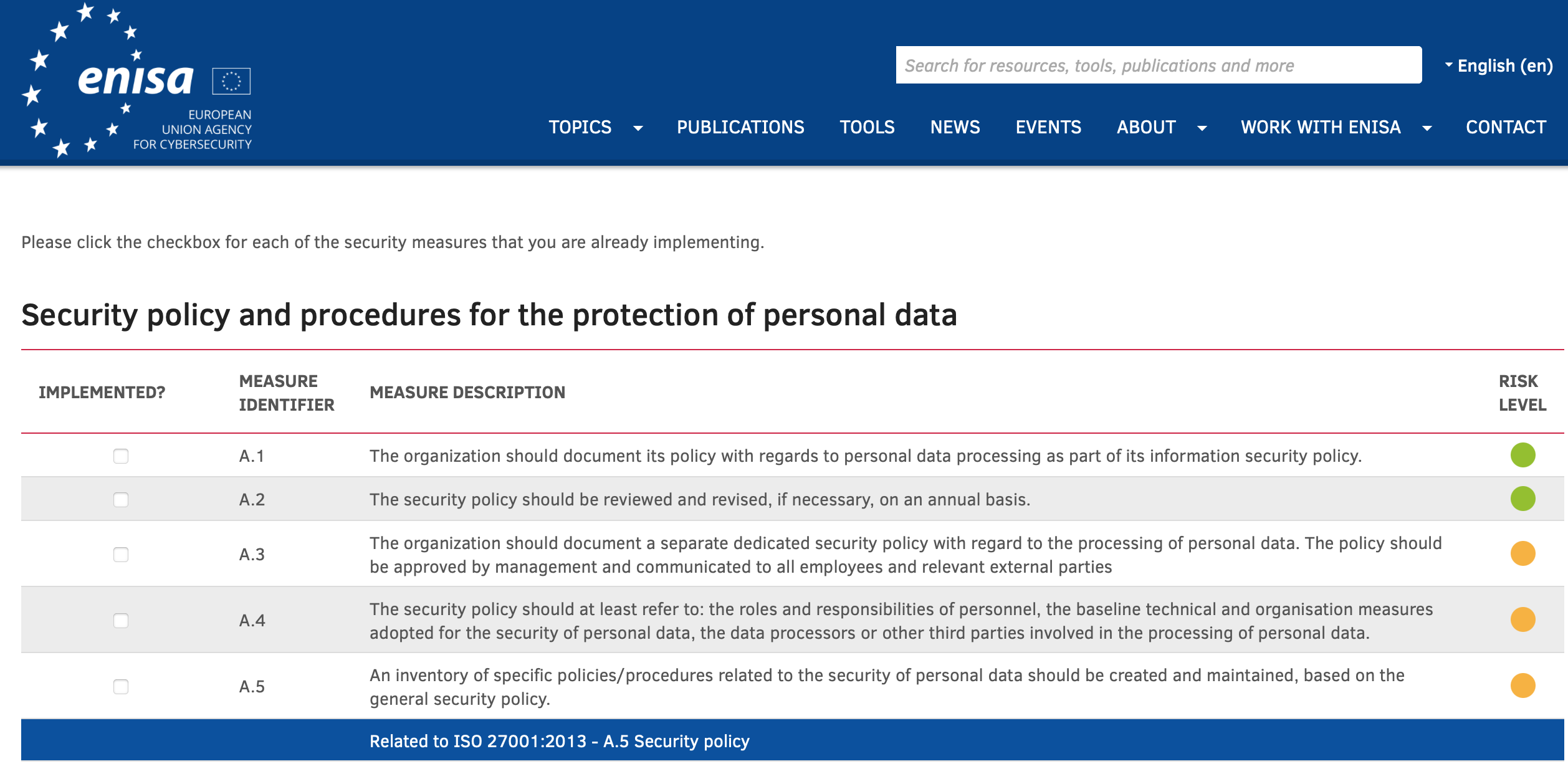 Figure 2. ENISA online tool for (self)assessing the implemented security measures.[9]
Figure 2. ENISA online tool for (self)assessing the implemented security measures.[9]
| Example: The project coordinator concludes that undefined roles and responsibilities with regards to the data processing in the project pose a medium risk. Upon consulting ISO 27001:2013 – A.6.1.1 Information security roles and responsibilities, the project appoints a security officer. This security officer is responsible to define, communicate and oversee all roles and responsibilities in the project that relate to data processing. This includes for instance making sure that employees leaving the project have their access to the data revoked. |
It needs to be emphasized that the creation of cybersecurity is not an easy task, particularly not for researchers and research projects, given the limited financial and human resources. Nonetheless, regulatory requirements for data protection and information security calls for standardized processes that researchers can take to analyze and mitigate risks. There exists no one-size-fits-all solution and researchers need to be aware of specific additional regulations and requirements in their sector. ENISA and other EU bodies and data protection authorities offer additional guidance on the application of cybersecurity measures that researchers are advised to seek in the interest of stakeholders and data subjects.[10]
To Dos
|
References
1Bundesamt für Sicherheit in der Informationstechnik. 2017. BSI-Standard 200-2 on IT-Grundschutz methodology (formerly known as IT baseline protection manual) Available under: https://www.bsi.bund.de/SharedDocs/Downloads/EN/BSI/Grundschutz/International/bsi-standard-2002_en_pdf.pdf?__blob=publicationFile&v=2 (Last accessed: 11.11.2021) ↑
2See for instance ISO/SAE 21434 “Road vehicles – Cybersecurity engineering” or ETSI EN 303 645 for IoT-devices. ↑
3ENISA. Overview of the methodology. Available under: https://www.enisa.europa.eu/risk-level-tool/methodology (Last accessed: 03.11.2021) ↑
4A more detailed version of the guidelines can be found here: https://www.enisa.europa.eu/publications/guidelines-for-smes-on-the-security-of-personal-data-processing (Last accessed: 03.11.2021) ↑
5ENISA. Overview of the methodology. Available under: https://www.enisa.europa.eu/risk-level-tool/methodology (Last accessed: 03.11.2021) ↑
6It needs to be emphasized that, although the process deals with data protection and personal data, this process is not a data protection impact assessment (DPIA under GDPR Art.35). This assessment focuses solely on cybersecurity whereas a DPIA encompasses additional parameters. ↑
7Ibid. ↑
8Art. 32 (and Art. 24) GDPR Security of processing does also mention technical and organizational measures and lists some exemplary measures for data processing of personal data. This includes pseudonymization and encryption of data (Art. 32(1)(a) GDPR). ↑
9ENISA. (Self)assessing the implemented security measures. Available under: https://www.enisa.europa.eu/risk-level-tool/assessment (Last accessed: 05.11.2021) ↑
10ENISA. Additional tools and guidance for specific sectors and industries are available here: https://www.enisa.europa.eu/tools (Last accessed: 05.11.2021) ↑
